Security hotspots
On this page
A security hotspot highlights a security-sensitive piece of code that the developer needs to review. Upon review, you'll either find there is no threat or you need to apply a fix to secure the code. For more information about Security Hotspots, take a look at the SonarQube Server, SonarQube Cloud, and SonarQube Community Build documentation.
Hotspot analysis
It is possible to locally detect and report hotspots in SonarQube for Visual Studio for C, C++, and JS/TS languages. Requirements include running SonarQube for Visual Studio in Connected mode and being bound to a project in SonarQube 9.9 or newer, or to a project on SonarQube Cloud. Security hotspot analysis rules are run each time a local analysis is triggered.
Locally detected hotspots are differentiated from those found on the server in the SonarQube Security Hotspots view window by the addition of the SonarQube Server icon, or the SonarQube Cloud icon. The hotspot’s location is also noted in the tooltip, revealed when hovering over the item.
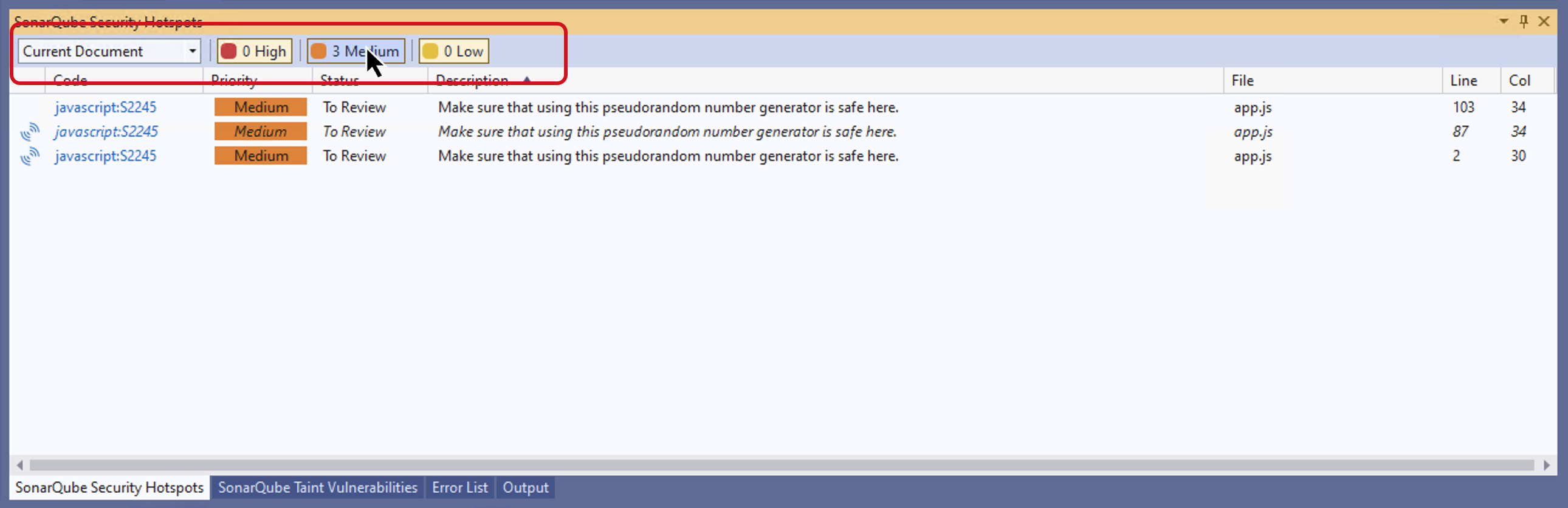
In addition, hotspots can be filtered by Current Document or Open Documents, and sorted by Priority if desired.
Newly detected Hotspots
Locally found hotspots will be highlighted in the editor using the characteristic SonarQube for Visual Studio squiggles. In addition, a list of all locally found hotspots will be found in the new Local Security Hotspots tool window, which will open and close automatically when there is a local hotspot to report. Selecting the rule key of your hotspot in the SonarQube Local Security Hotspots tool window will open the SonarQube Rule Help window where you can review descriptive and educational content associated with the hotspot.
Already known hotspots
Hotspots already detected by the SonarQube (Server, Cloud) or SonarQube Community Build are identifiable by the addition of the 

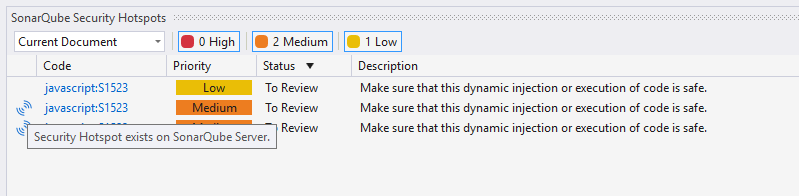
It’s possible to open a security hotspot found on SonarQube Server directly from your IDE. Simply right-click on the hotspot and select Review Security Hotspot.
Open in IDE from SonarQube
SonarQube for Visual Studio provides a way to investigate Security hotspots found on SonarQube Server. This is an integration feature: when viewing a hotspot on SonarQube Server, you will notice a button named Open in IDE; selecting that button while Visual Studio is running will open the hotspot's code file in the IDE.
See the Opening issues in the IDE article to see how it looks in SonarQube Server. Unfortunately, the SonarQube Cloud Open in IDE feature is not available for security hotspots at this time.
Feature requirements
- SonarQube Server version 9.9 or higher.
- SonarQube for Visual Studio version 4.29 or higher.
- The correct solution must be open in Visual Studio and it must be running in Connected mode. SonarQube Server will not open Visual Studio if it is closed.
- Open in IDE is not yet supported in SonarQube Cloud.
Feature overview
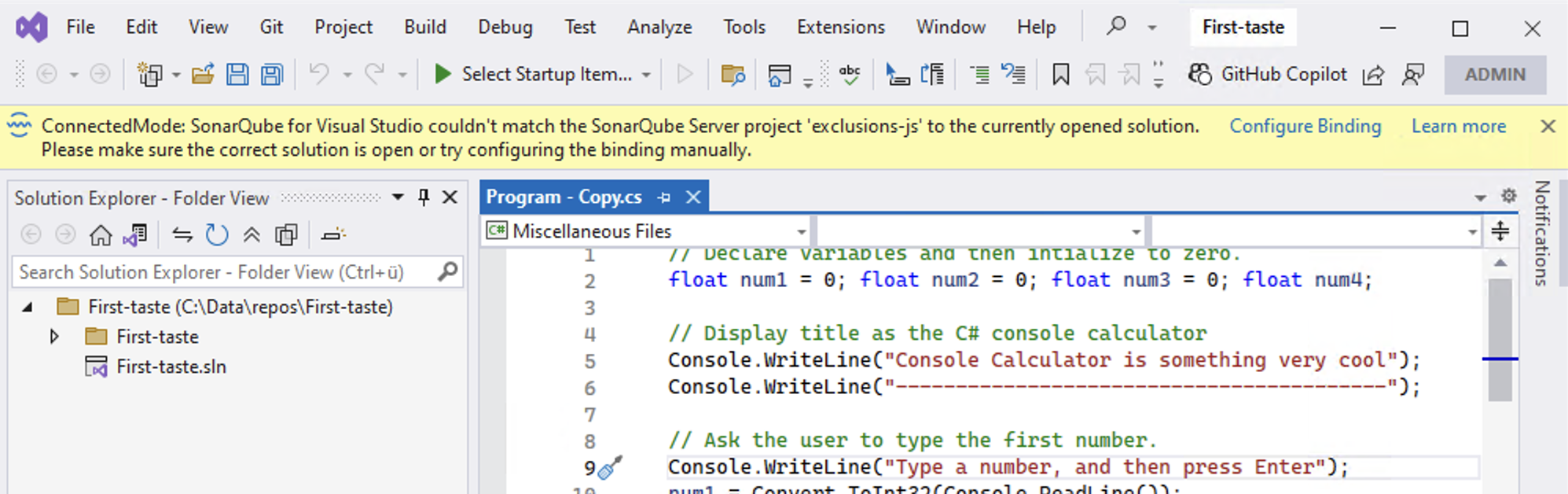
When SonarQube for Visual Studio receives an Open in IDE request from the browser, SonarQube for Visual Studio will verify that the correct solution is open in connected mode. If not, a gold bar will be displayed asking you to check if you've got the correct solution open, or to try and configure the binding manually:
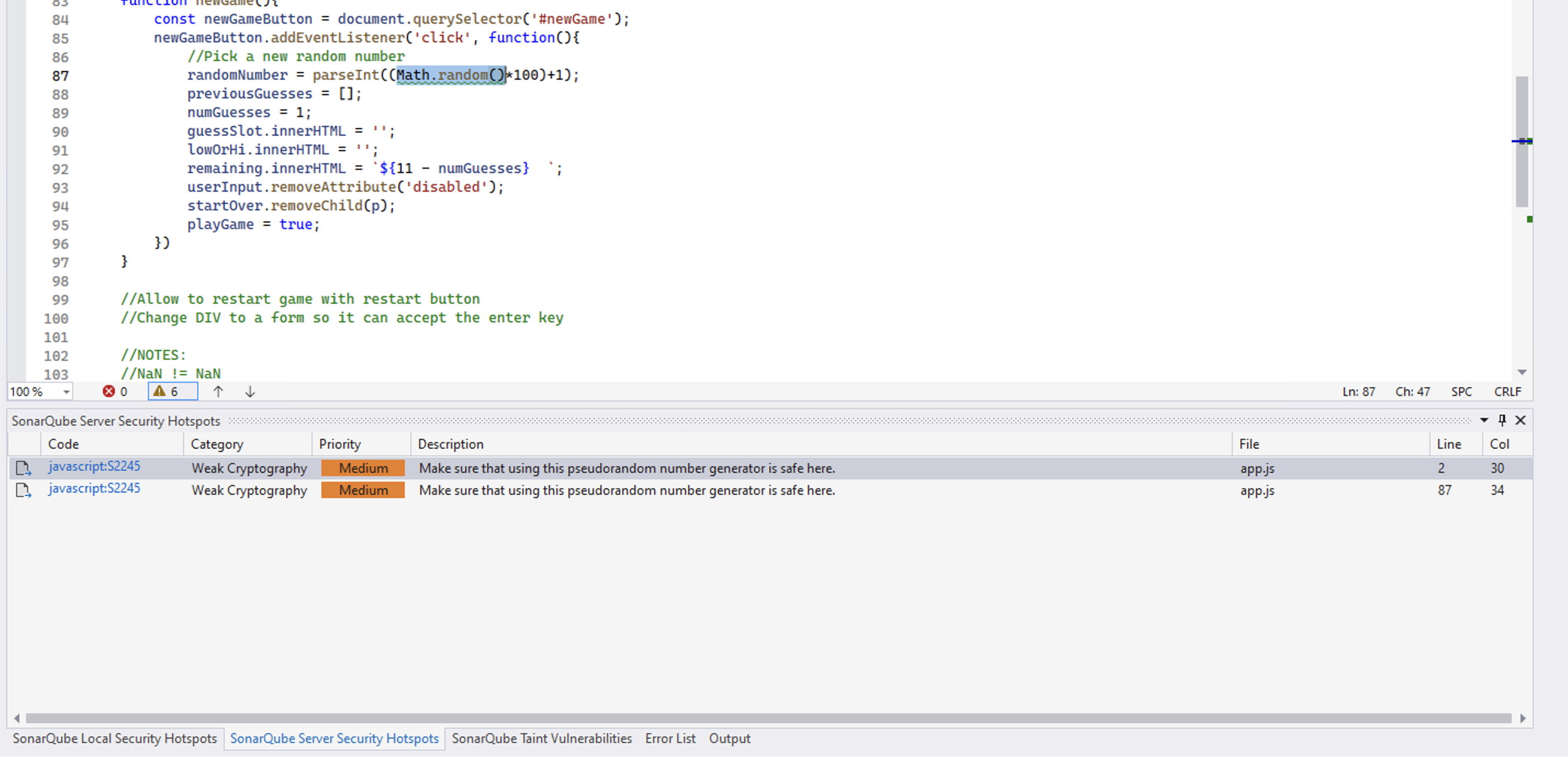
If the correct solution is open and the hotpot's code location can be found in the solution, SonarQube for Visual Studio will open the file and navigate to the relevant code. In addition, the hotspot is added to the SonarQube Local Security Hotspots tool window where you will find additional information:
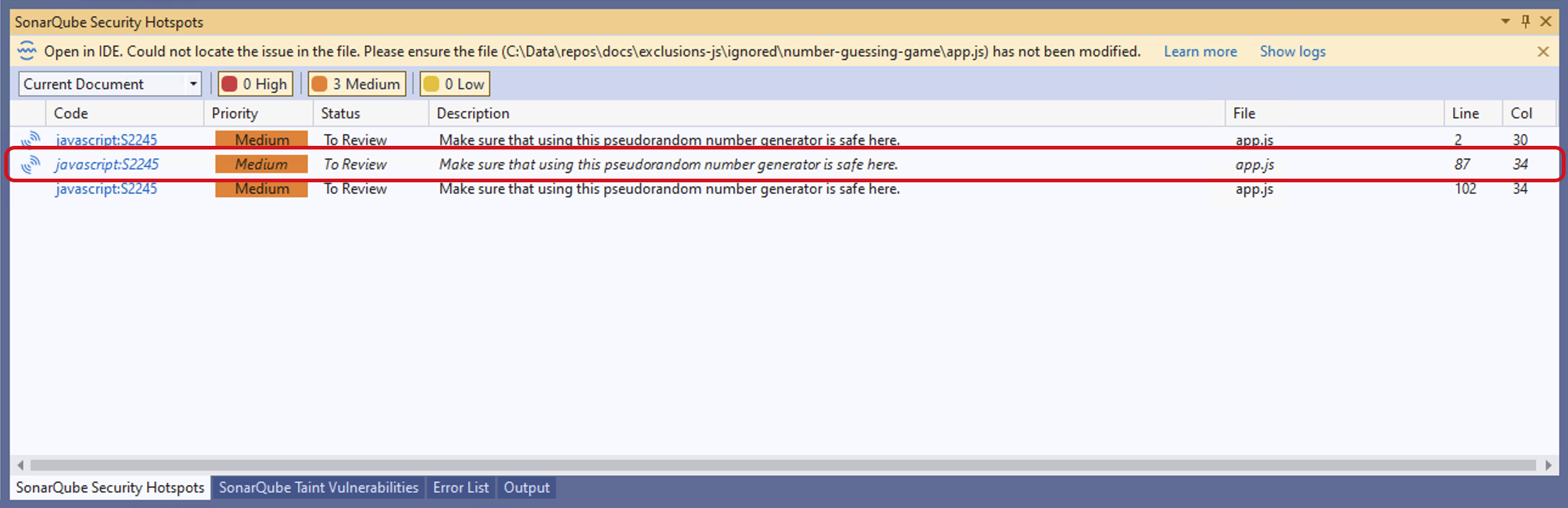
It is possible that the code on SonarQube Server does not match your local code version. For example, if code changes have been made since the last analysis or if the relevant code project is not included in the solution, SonarQube for Visual Studio cannot find what does not exist locally. In this case, SonarQube for Visual Studio will show the hotspot as being on the server (using the 

Security Hotspots list functionality
Once a hotspot has been added to the list, you can navigate to it using a double-click or the Enter key. In addition, your list of security hotspots can be filtered by Current or Open documents, or by a combination of Priority levels:
Implementation notes
When Visual Studio starts, SonarQube for Visual Studio will start listening in the background for Open in IDE requests originating from your local browser. This listener does not require a lot of resources and should not affect your machine's performance and memory consumption in any way, nor should it interfere with your work. SonarQube for Visual Studio will try to find an available port in the range 64120-64130 inclusive. Information about the port selection will be logged in the SonarQube for Visual Studio pane in the Output Window. If a port cannot be found, Open in IDE will not be handled. The port range is not configurable.
Was this page helpful?