Encrypting Helm chart sensitive data
You can encrypt any sonar property stored in the values.yaml file and some Helm parameters, such as jdbcPassword, that will be managed as sonar properties.
You must have the Administer System permission in SonarQube Community Build to perform this procedure.
Prerequisites
SonarQube Community Build must be up and running.
Step 1: Create the encryption key
- In SonarQube Community Build UI, go to Administration > Configuration > Encryption.
- Select Generate Secret Key. An encryption key is generated.
- Store the generated key in a safe location.
Step 2: Create a Kubernetes secret to store the encryption key
Use the command below:
kubectl create secret generic --from-literal sonar-secret.txt=<encryptionKeyValue> <encryptionKeySecretName>Example:
kubectl create secret generic --from-literal sonar-secret.txt=EgycYJc4Ek4uj2pH39e3+bnnk15IrVu4dxtfjDyN1y8= myEncryptionKeySecretStep 3: Enable the encryption in the Helm chart
Install the encryption key secret as follows:
1. Add the following to the values.yaml file:
sonarSecretKey: <encryptionKeySecretName>2. Use the helm upgrade command.
Step 4: Encrypt the sensitive data
To encrypt a sensitive property in values.yaml:
1. In SonarQube Community Build UI, go to Administration > Configuration > Encryption.
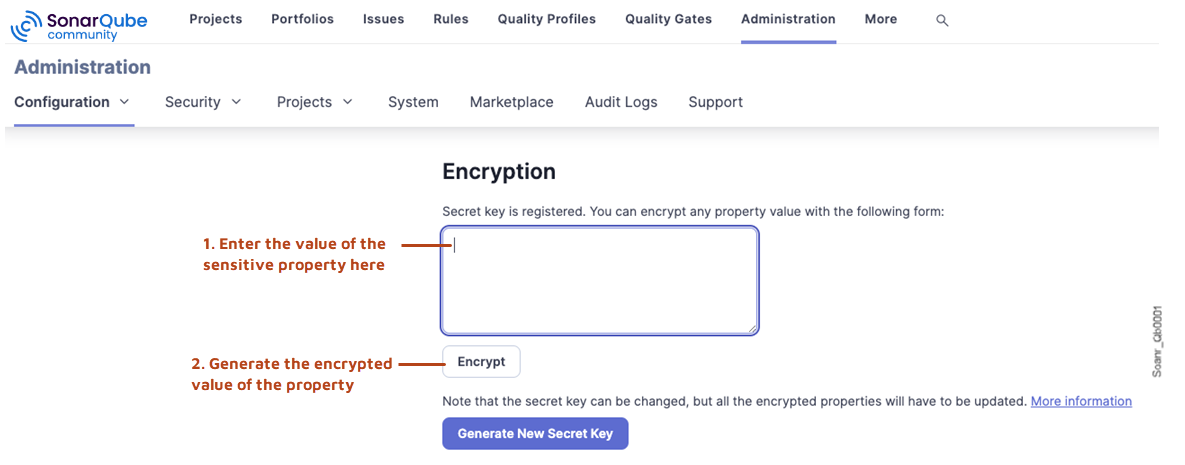
2. Enter the value of the property.
3. Select the Encrypt button. The encrypted value of the property is generated.
4. Select the copy tool.
5. In the values.yaml file, replace the value of the property with the copied encrypted value.
6. Use the helm upgrade command.
Was this page helpful?