VS Code | Using SonarQube for IDE | Dependency risks
Dependency risks
In connected mode, you can see the results from SonarQube Server’s Software composition analysis (SCA) directly in the SonarQube for VS Code UI. This includes:
- vulnerabilities in your third-party open source dependencies
- where your open source dependencies may conflict with your organization’s license policies
Prerequisites
- SonarQube Server Enterprise edition, version 2025.4 or later.
- Advanced Security add-on with the SCA feature enabled on your SonarQube Server instance.
- Running SonarQube for VS Code in connected mode with SonarQube Server. See the pages on Connected mode and Connected mode setup for more details.
How to view your dependency risks
In SonarQube for VS Code, dependency risks are displayed in the SONARQUBE Panel.
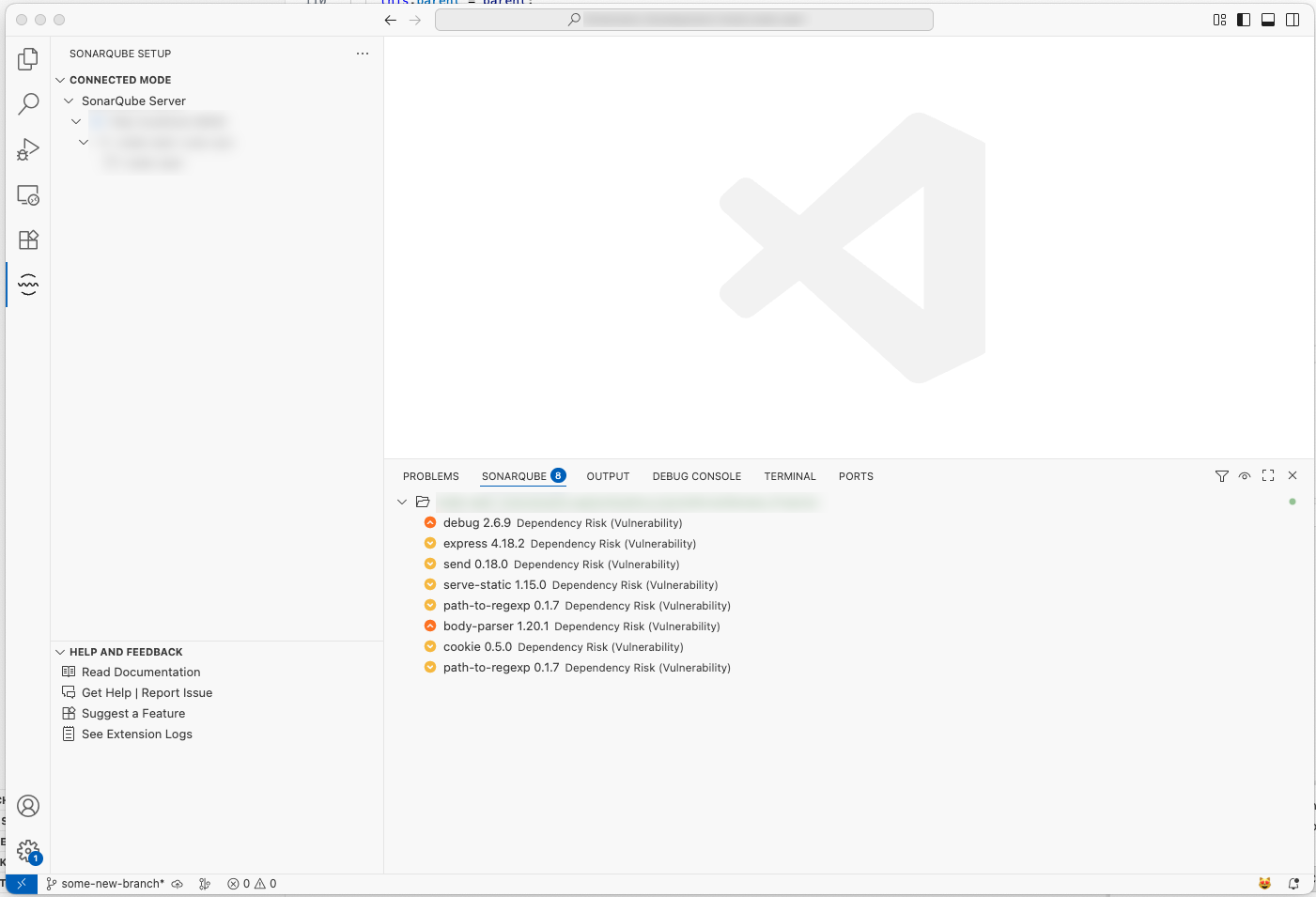
For each dependency risk, the following information is displayed:
- Risk type: Vulnerability and Prohibited license
- Risk severity: Blocker, High, Medium, Low, or Info
- Package name
- Package version
You can select a risk to open it in SonarQube Server to get more details.
Fixing dependency risks
Because dependency risk analysis requires that you run in connected mode, any changes you make to the code must be analyzed by your instance of SonarQube Server. Here are two options to resolve dependency risks displayed by SonarQube for VS Code:
- After you fix the dependency risk in your IDE, commit your code to the server and rerun the analysis on SonarQube Server. The new status of the risk will be reflected in your IDE.
- Mark the dependency risk as Confirmed, Accepted, or Safe directly from the VS Code UI or in SonarQube Server. You can also add comments. The status update is then reflected in VS Code or SonarQube Server.
Was this page helpful?