Rules and languages
The Sonar Rules catalog is the entry point where you can discover all the existing rules. While running an analysis, SonarQube for IDE raises an issue every time a piece of code breaks a coding rule. Software quality classification and severity show the impact of the issue on your code.
See Software qualities for more information.
Overview
SonarQube for the JetBrains family IDEs currently supports the following programming languages:


| Language | IntelliJ IDEA & Android Studio | CLion | Rider | (DataGrip, Php Storm, PyCharm, RubyMine, and WebStorm) |
|---|---|---|---|---|
| C# |  | |||
| C/C++ |  | |||
| CSS |  |  |  | |
| Go |  (Go plugin) (Go plugin) |  (GoLand or Go plugin) (GoLand or Go plugin) | ||
| HTML |  |  |  | |
| Java |  | |||
| JavaScript |  |  |  | |
| Kotlin |  |  | ||
| PHP |  |  | ||
| PL/SQL |  (Database Tools plugin) |  (Database Tools plugin) |  (Database Tools plugin) | |
| Python |  |  | ||
| Ruby |  |  | ||
| Scala |  |  | ||
| Secrets |  |  |  |  |
| Swift |  |  | ||
| TypeScript |  |  |  | |
| XML |  |  |
In addition, SonarQube for IntelliJ supports the IaC domains for:
| Language | IntelliJ IDEA & Android Studio | CLion | Rider | (DataGrip, Php Storm, PyCharm, RubyMine, and WebStorm) |
|---|---|---|---|---|
| Ansible |  |  |  |  |
| CloudFormation |  |  | ||
| Docker |  |  | ||
| Kubernetes |  |  | ||
| Terraform |  |  |
Supported language versions
Supported language versions
SonarQube for intelliJ provides analysis for several languages. Support for your language may vary depending on the SonarQube for IntelliJ version you're running.
The table below lists the supported language and language versions. For each language version, the level of support is defined as follows:
- Fully supported: Analysis will complete. All the language features are understood and examined.
- Supported: Most language features are understood and examined but the version includes unsupported features. Analysis might break or provide incomplete results.
For language-specific properties, refer to the relevant language page in SonarQube Server and SonarQube Cloud directly, as the same Sonar language analyzers are used by SonarQube for IntelliJ.


| Language | Supported version | |
|---|---|---|
| Ansible |  | - |
| C |  | C89, C99, C11, C17: Fully supported C23: Supported GNU extensions: Supported |
| C# |  | C#1 to C#12: Fully supported |
| C++ |  | C++20, C++23: Supported C++03, C++11, C++14, C++17: Fully supported GNU extensions: Supported |
| CloudFormation |  | 2010-09-09: Supported |
| CSS |  | - |
| Docker |  | - |
| Go |  | - |
| HTML |  | - |
| Java |  | Java LTS versions 8 to 21, and all intermediate versions up to Java 23: Fully supported |
| Javascript |  | ECMAScript 2022 and all previous versions: Supported. |
| Kotlin |  | 1.3 to 2.0: Supported |
| Kubernetes |  | - |
| PHP |  | 5.x, 7.x, and 8.4: Fully supported |
| PL/SQL |  | - |
| Python |  | 2.7: supported 3.0 to 3.12: Fully supported |
| Ruby |  | 3.0 to 3.2: Supported |
| Scala |  | - |
| Secrets |  | - |
| Swift |  | 5.9: supported 3.x, 4.x, 5.7, and 5.8: Fully supported |
| Terraform |  | - |
| TypeScript |  | TypeScript 5.6 and all previous versions: Supported |
| XML |  | - |
For more details about languages and new features under consideration for the JetBrains family IDEs, you can refer to the SonarQube for IDE roadmap where we list all of our coming soon and newly released features.
Rule selection
The full list of available rules is found by navigating to the IntelliJ Settings... > Tools > SonarQube for IDE> Rules tab. There, Sonar Rules can individually be turned on or off while running SonarQube for IDE in standalone mode; simply select or deselect the appropriate checkbox.
When your project is bound to SonarQube Server or SonarQube Cloud using Connected Mode, the rule set is managed on the server side as defined by the quality profile.
When a project is bound to a SonarQube Server instance or SonarQube Cloud, the configuration in this UI location is ignored. In this case, rules configuration from the server applies. See the SonarQube Server and SonarQube Cloud documentation about quality profiles for more information.
Sonar Rule Descriptions
Simply select an issue in the SonarQube for IDE view or choose SonarQube for IDE: Show rule description from the tooltip to open the Rule tab. Here, you will find a brief explanation of the rule as well as Noncompliant and Compliant code samples.
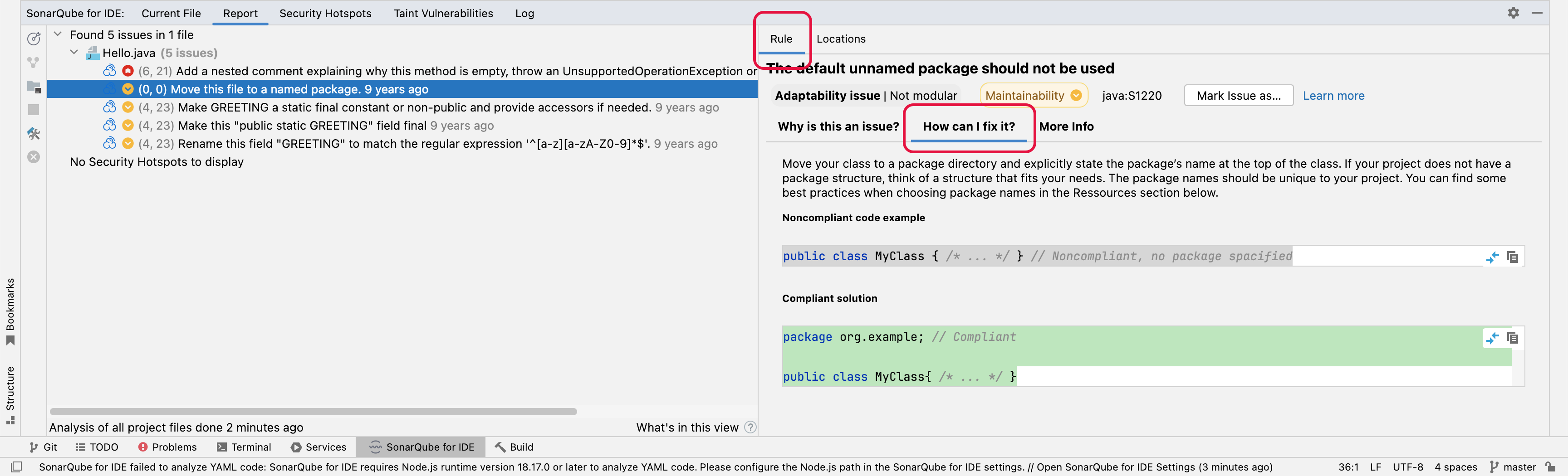
SonarQube for IntelliJ supports syntax highlighting. In addition, users are able to visualize a diff view for the non & compliant code samples which should help you fix your issue. Note that diff highlighting is only available for rules descriptions migrated to the new format, and we're progressively migrating all existing rules to the new format.
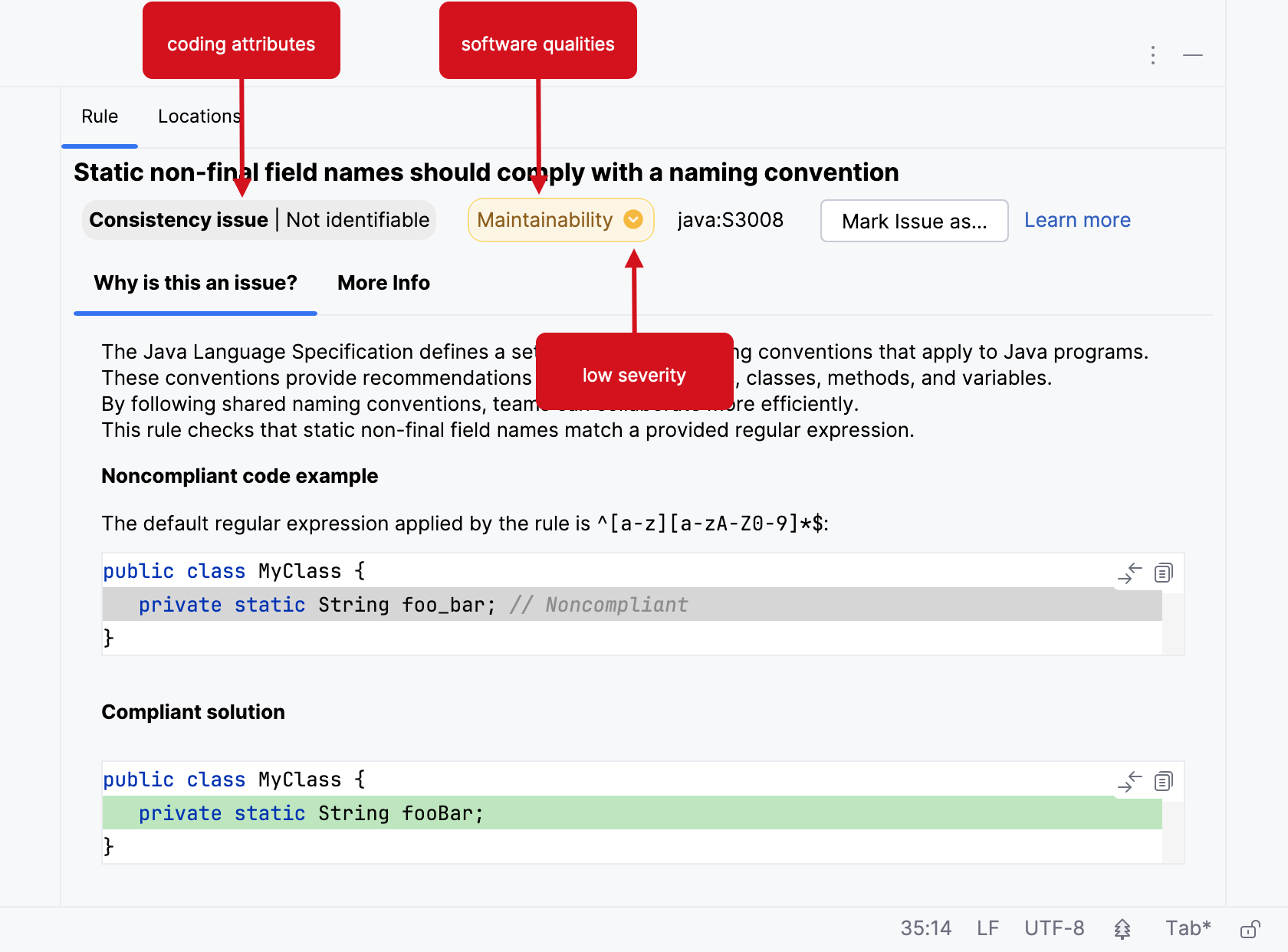
An issue’s coding attribute, software qualities, and severity are found when opening the SonarQube Rule tab. Below the rule title, you will find the coding attributes that highlight an issue's classification. Check the glossary for details about coding attributes, and the Software qualities page to better understand how they help classify your issue.
When in Connected Mode
If you’re running SonarQube for IntelliJ while in connected mode with SonarQube Server or SonarQube Community Build, your view will change according to the server settings. Standard Experience mode encompasses the use of rule types such as bugs, code smells, and vulnerabilities. Alternatively, if SonarQube Server is set to Multi-Quality Rule mode, you will more accurately represent the impact an issue has on all software qualities.
Please see the SonarQube Server and SonarQube Community Build articles for detailed information about the available rule modes.
Be sure to check out the Investigating issues page for more details about how issues appear in your IDE.
Applying rules while in Connected Mode
Connected Mode syncs your SonarQube Server or SonarQube Cloud Quality Profile with the local analysis to suppress issues reported in the IDE. Therefore, when running in Connected Mode, SonarQube for intelliJ will ignore rule settings that are defined locally. See the Connected Mode page for more information about running Connected Mode.
C# analysis
The SonarSource C# analyzer is written as a Roslyn analyzer and requires the use of the JetBrains Rider IDE. Please see the Supported features in Rider article for more information.
Go
SonarQube for IntelliJ will check your code against Go rules using either GoLand or the Go plugin extension for IntelliJ.
JS/TS/CSS analysis
The analysis of JavaScript, TypeScript, and CSS code requires Node.js >= 16; Node.js >= 18 is recommended.
PL/SQL analysis
The support for PL/SQL analysis is only available together with Commercial Editions of SonarQube Server or with SonarQube Cloud when running in Connected Mode. In addition, the Database Tools extension is required to complete the local analysis in IntelliJ IDEA, CLion, or WebStorm.
Rules for AI CodeFix
A select set of rules are eligible for AI CodeFix when running in connected mode. Please see the Rules covered with AI CodeFix article for a full list.
Other rule types
DBD rules
Dataflow bugs are what Sonar calls a series of advanced Python and Java bugs using symbolic execution. This type of issue can cause runtime errors and crashes in Python and Java. If you want to learn more, check out our blog post for a good explanation with an example.
Dataflow Bug Detection (DBD) rules for Python and Java are supported in Commercial Editions of SonarQube Server. At this time, SonarQube for IntelliJ supports DBD detection for Python and Java when running in Connected Mode with SonarQube Server Active versions.
Injection vulnerabilities
Security vulnerabilities requiring taint engine analysis (injection vulnerabilities) are only available in Connected Mode because SonarQube for IDE pulls them from SonarQube Server or SonarQube Cloud following a project analysis.
To browse injection vulnerabilities in SonarQube for IntelliJ, configure connected mode with your SonarQube Server commercial edition or SonarQube Cloud instance. Once a Project binding is configured, SonarQube for IDE will synchronize with the SonarQube Server instance or SonarQube Cloud server to report the detected injection vulnerabilities.
More information about security-related rules is available in the SonarQube Server or SonarQube Cloud documentation.
Security hotspots
In SonarQube for IntelliJ, local detection of Security Hotspots is enabled if you are using Connected mode with SonarQube Server or SonarQube Cloud.
Please see the SonarQube Server documentation on Security hotspots for more details.
Secrets detection
Secrets are pieces of user-specific or system-level credentials that should be protected and accessible to legitimate users only. SonarQube for IDE detects exposed Secrets in your source code and language-agnostic config files. When running in Connected Mode, the SonarQube Server or SonarQube Cloud Quality Profiles are applied to locally detected Secrets.
Was this page helpful?