10.7 | Instance administration | Authentication and provisioning | SAML | With Ping Identity (Beta) | Setup of security features
Setting up optional security features for SAML with a Ping Identity provider
Once you have registered SonarQube in PingOne or PingFederate, you can set up the following security features:
- The encryption of SAML assertions emitted by the Ping Identity provider for SonarQube.
- The signing of the SAML requests from SonarQube to the Ping Identity provider.
Setting up the encryption of SAML assertions
To enable the encryption of SAML assertions, you need to provide two things:
- Service provider private key: PKCS8-stored private key used for signing the requests and decrypting responses from the identity provider.
- Service provider certificate: X.509 certificate for the service provider used for signing the requests.
Follow the steps below.
Step 1: Generate the private key and certificate
- On the machine running SonarQube server, open a command line.
- Generate a Certificate Signing Request (CSR) with a new private key and certificate request.
Example:
openssl req -sha256 -nodes -newkey rsa:2048 -keyout sonar.key -out sonar.csrwhere:
sonar.keyis the name of the private key output.sonar.csris the name of the certificate request output.
- Press Enter. You will be presented with a series of prompts.
- Input Country, State, etc. Make sure that the server FQDN input matches your SonarQube server base URL.
- Convert the certificate request into PEM format.
Example:
openssl req -inform PEM -in sonar.csr -out sonar.pemwhere:
sonar.csris the certificate request from the previous step.sonar.pemis the name of the converted CSR output.
- Generate a self-signed certificate starting from an existing certificate as a CRT file.
Example:
openssl x509 -req -in sonar.pem -signkey sonar.key -out sonar.crtwhere:
sonar.pemis the CSR in PEM format from the previous step.sonar.keyis the private key from the previous step.sonar.crtis the final self-signed certificate output.
- Convert the private key to PKCS#8 format using the following command:
openssl pkcs8 -topk8 -in sonar.key -out pkcs8.key -nocrypt
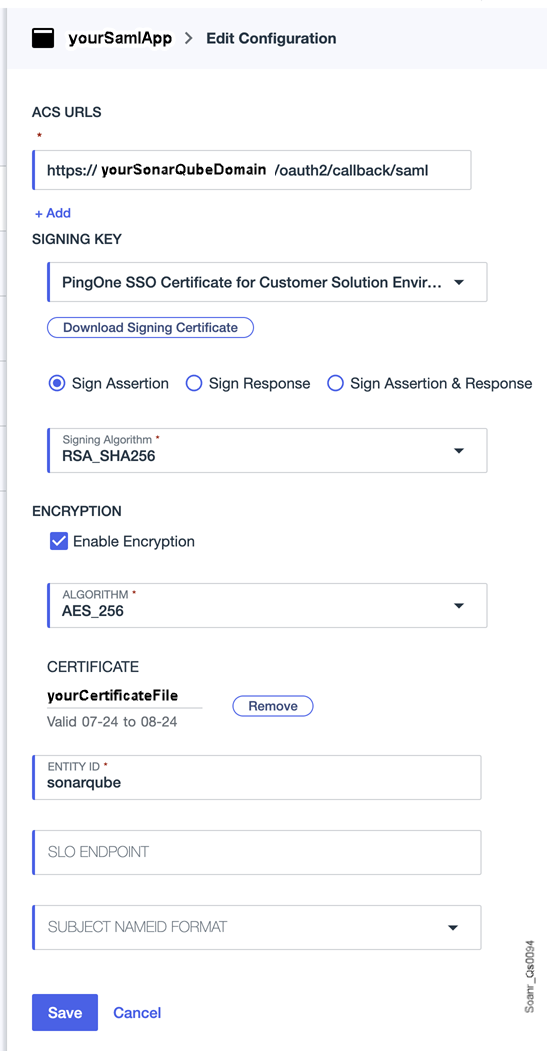
Step 2: Configure the encryption in the Ping Identity provider
- In PingOne, retrieve the SAML application you created in Registering SonarQube in Ping Identity (To do so, go to Applications > Applications and open the SAML application's details page).
- Go to the Configuration tab.
- Select the pencil icon.
- In the Encryption section:
- Select Enable Encryption.
- In Algorithm, set AES_256.
- In Certificate, upload the provider certificate file generated in step 1 above.
- Select Save.
Step 3: Configure the encryption in SonarQube
- Go to Administration > Configuration > General Settings > Authentication > SAML.
- In SAML Configuration > SAML, select Edit. The Edit SAML configuration dialog opens.
- Copy the PKCS8 private key file contents.
- Paste it in Service provider private key.
- Copy the self-signed certificate contents.
- Paste it in Service provider certificate.
- Select Save configuration.
- Select Test Configuration.
Setting up the signing of SAML requests
You can set up the signing and verification of the SAML requests sent by SonarQube to the Ping Identity provider. To do so:
- Set up the encryption of SAML assertions as explained above.
- In SonarQube, do the following additional setting: In the SAML configuration, select the Sign requests option.
Related pages
Was this page helpful?