Reviewing and fixing dependency risks
SonarQube lets you manage the dependency risks detected during analysis and provides insights on how to fix them.
Advanced Security is available in SonarQube Server as an add-on starting in Enterprise edition.
Permissions
On private projects, applications, and portfolios, the following permissions apply:
Browse: access, browse, confirm dependency risks, change assignee.
Administer issues: change risk severity, resolve risks as Accepted or Safe.
Anyone is allowed to browse dependency risks on public projects, applications and portfolios.
Changing the status of a dependency risk requires the Administer Issues permission.
Reviewing and fixing dependency risks
Navigate to the Dependency Risks tab located under Projects, Applications and Portfolios.
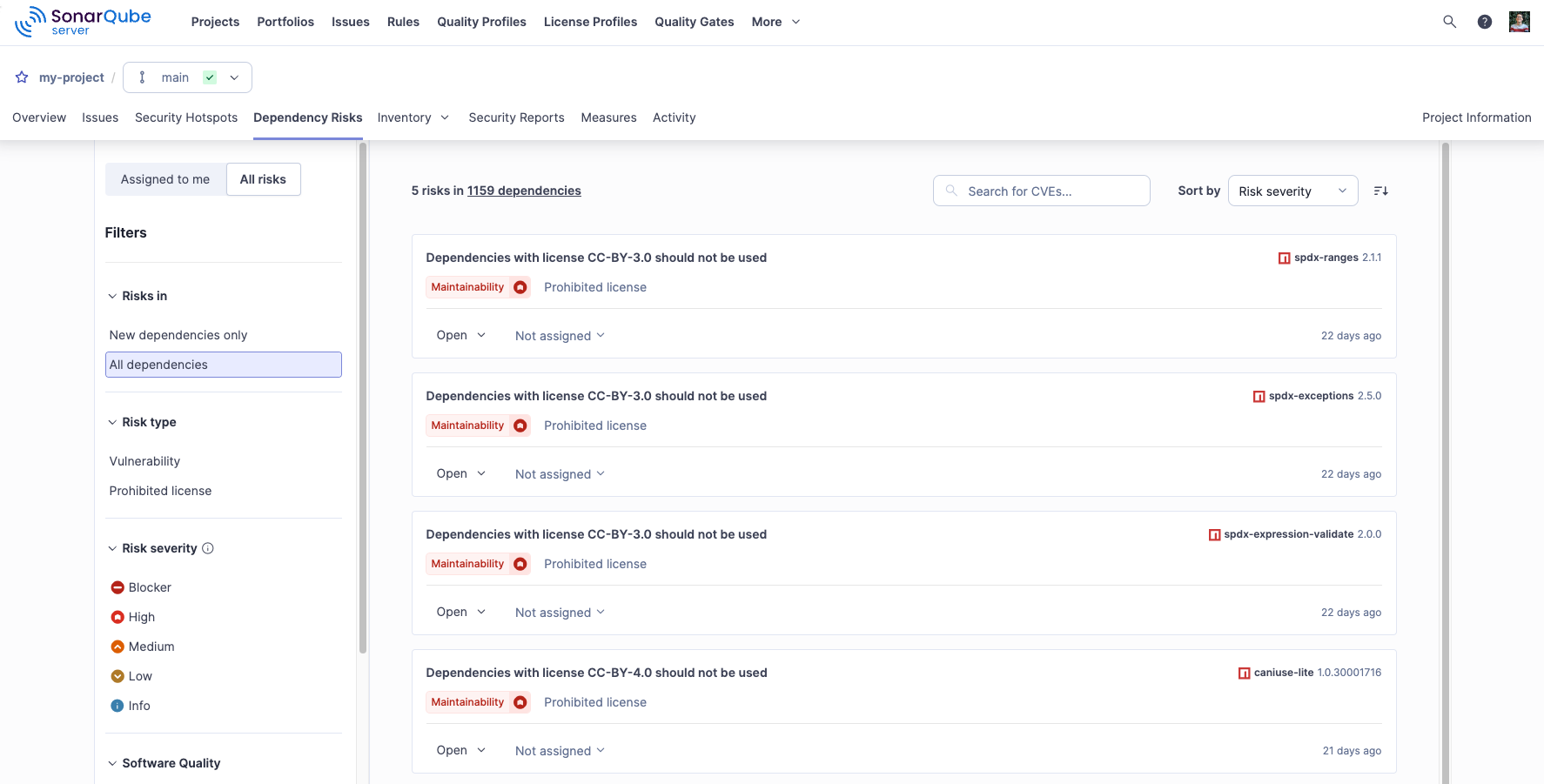
Use Filters in the left side bar to narrow down the results. You can filter the results by:
Risk type: Vulnerability, Malicious package, and Prohibited license
Risk severity: Blocker, High, Medium, Low, or Info
Software quality: Security, Maintainability
Dependency type: Direct or Transitive
Dependency scope: Production or Development
Package manager: See Analyzing projects for dependencies (SCA) for a list of supported package managers and languages.
Status: Accepted, Confirmed, Open, Fixed, Safe
Assignee: Type in the name of the person assigned and select it from the list.
From there, you can sort the list of results:
by choosing the sorting criteria from the Sort by dropdown menu
by vulnerability name by entering a vulnerability ID (such as CVE-2022-38392) into the search box
The following information is displayed for each dependency risk in the list:
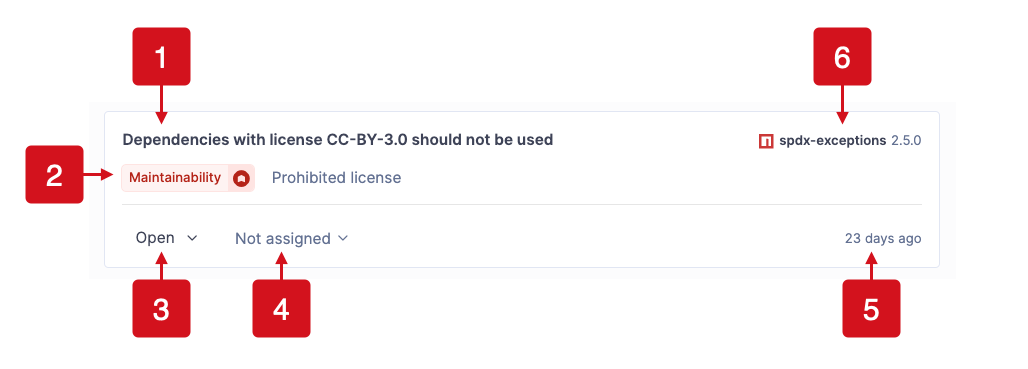
Descriptive title of the dependency risk. Click on the title to open a detailed view.
Software quality, risk type, and severity
Status: Open, Confirmed, Accepted, Safe
Assignee of the risk
Amount of time that has passed since the risk was first detected
Affected dependency and version
Understanding the risk types
Each dependency risk has an assigned risk type:
Vulnerability: When a third-party dependency is affected by a publicly reported vulnerability, such as a record on CVE.org
Malicious package: When a third-party dependency is known to be malicious
Prohibited License: When a third-party dependency has a software license not allowed by the project’s associated license profile and policy.
Changing dependency status and assigning risks
Dependency risk lifecycle
A dependency risk can have the following statuses:
Open: Initial state of a dependency risk after analysis. The risk has not been yet reviewed.
Confirmed: Indicates that the dependency risk has been reviewed and the risk is valid.
Accepted: The risk is valid but it may not be fixed for a while.
Safe: Indicates that the dependency risk does not compromise the security of the software. A mandatory justification must be provided.
To change the status of the dependency risk, click the Change Status button to open a modal. From the Status dropdown list select a new status for the risk and enter a description for the change in the Explain your decision text box.
Assigning a dependency risk
You can delegate a review of dependency risks to other team members by clicking the Unassigned dropdown menu and entering a name. You can also assign the risk to yourself.
Email notifications
If you have subscribed to email notifications for a project, note that the notifications that apply to issues also apply to dependency risks. For more information on notifications, see Notifications.
Detailed view
Clicking the title of the dependency risk in the list of results opens its detailed view page:
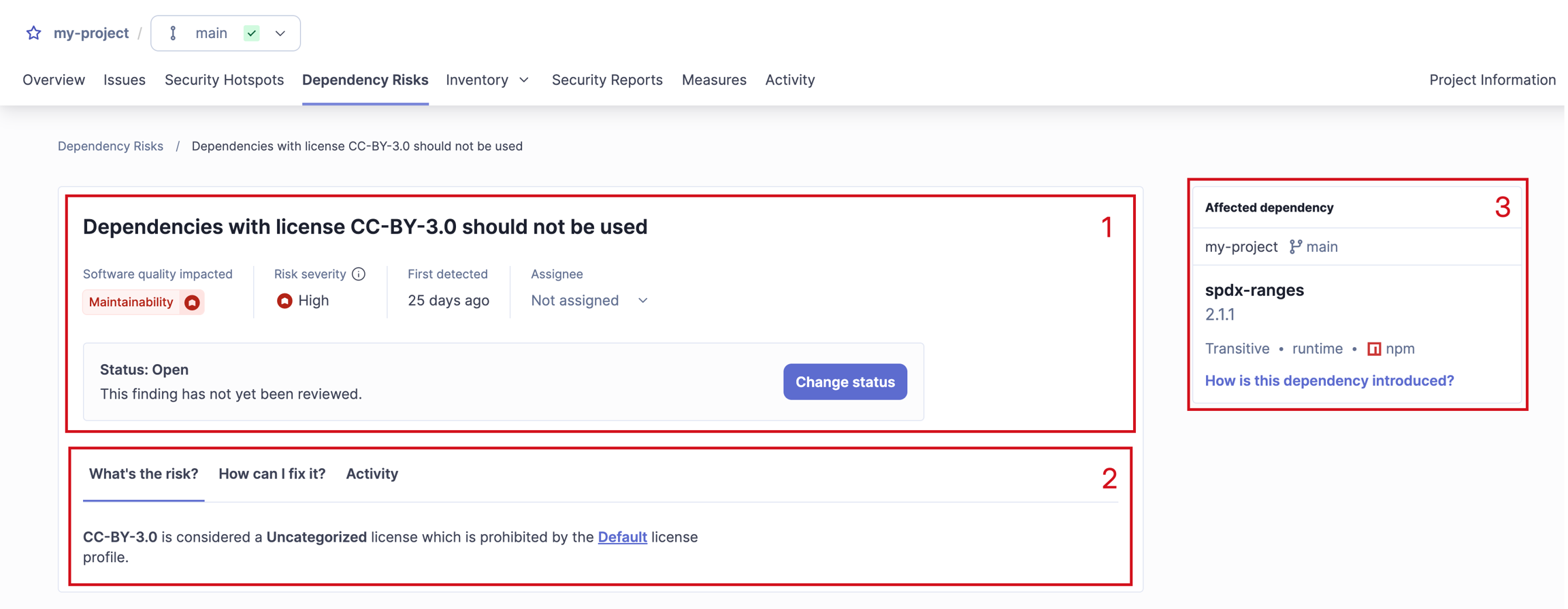
Details of the dependency risk, including Risk type, Risk Severity, First detected, Assignee, and Status.
What’s the Risk? and How can I fix it? allow you to review information about the dependency risk, the factors affecting the risk’s severity, and information about currently used dependency versions and fixes.
Affected dependencies shows the dependency version that raised the risk, dependency type, package manager and the associated risks. Click the View all risks for this dependency for a full list.
What’s the risk?
Sonar uses a holistic approach to determine the severity of a dependency risk. The methods used depend on the associated risk type.
Vulnerability risk
Sonar partners with select open source maintainers to uphold their software to secure development practices. As part of this partnership, Sonar-partnered maintainers provide guidance on vulnerabilities. This guidance includes:
Whether the vulnerability is real, or a false positive
How likely it is that the vulnerability will affect typical usage
Whether the vulnerability affects development or test usage, or only production usage
What workarounds, if any, are available
What specific functions or methods are affected
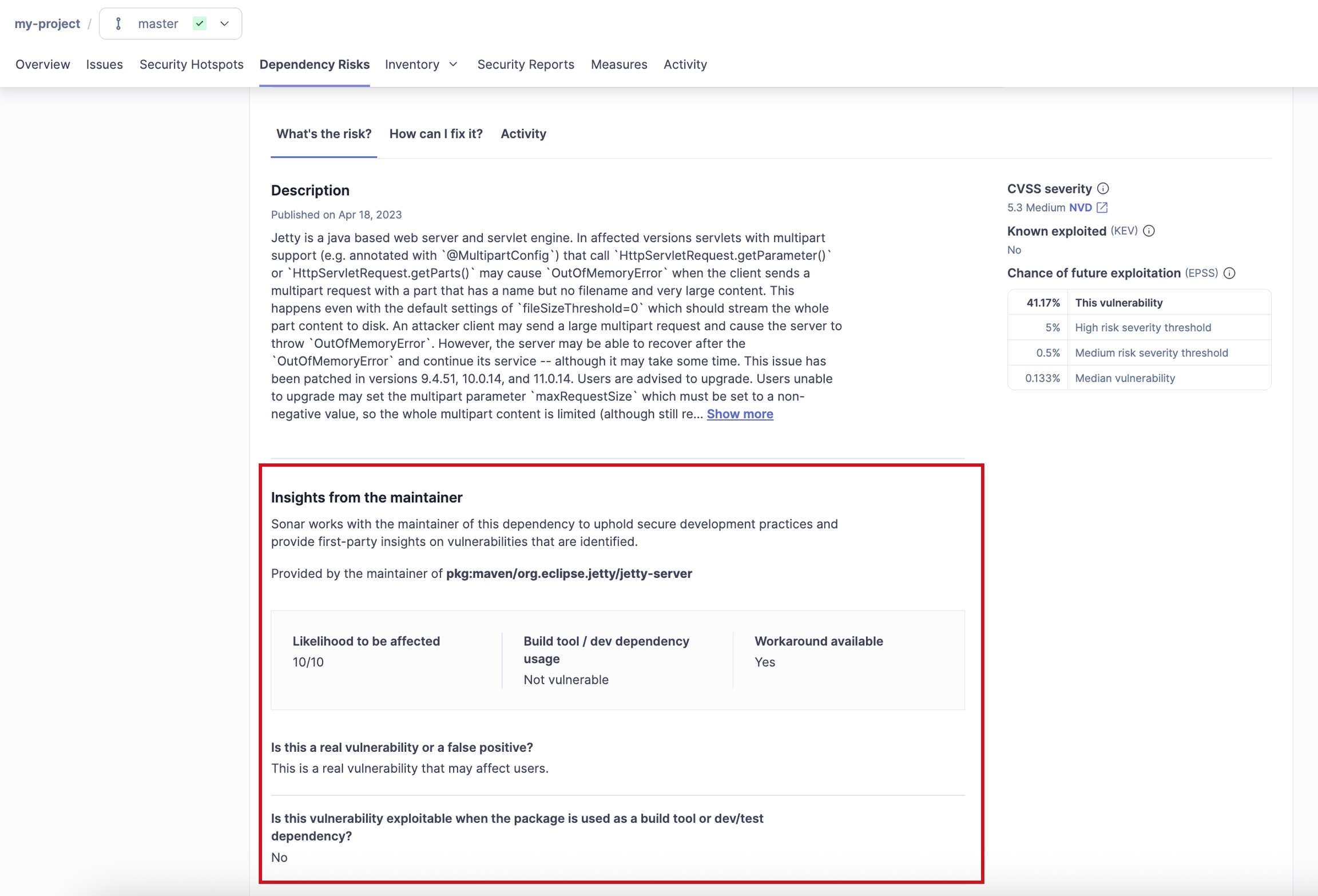
This guidance ensures that developers have comprehensive information to speed up remediation times.
Risk evaluation
The risk evaluation is based on the following factors:
Severity: Evaluates the technical severity of a vulnerability based on an assessment by CVSS.
Known exploited: Shows if the risk has been actively exploited in the wild. It’s measured by KEV.
Chance of future exploitation: Estimates the likelihood (percentage) of a software vulnerability being exploited in the wild over the next 30 days. It’s measured by EPSS.
Sonar combines these factors to assign a severity to a discovered vulnerability to ensure that developers are prioritizing the most urgent risk in their applications.
Malicious package risk
Malicious package risks are always BLOCKER severity. They should be remediated immediately.
Prohibited license risk
The dependency risk for prohibited license risk type depends on the configuration of your instance’s license profile and policy. The What’s the risk? tab provides information about the risk associated with the license and links to relevant resources. For more information, see Managing license profiles and policies.
Dependency risk severities
The table below lists the dependency risk severities used for vulnerability risks and their definition.
Risk severity
Definition
Blocker
A vulnerability is on the CISA KEV list.
High
Vulnerability has both:
• High exploitability (an EPSS probability greater than 5%)
• High risk (a CVSS score over 7.0)
Medium
Any other vulnerability that has both:
• Moderate or unknown exploitability (an EPSS probability greater than 0.5%, or no EPSS scoring)
• Moderate risk (a CVSS score over 4.0)
Low
Any remaining vulnerability that does not fit into another category.
Info
Any of the following is true:
• A Tidelift or Sonar partnered maintainer has declared the vulnerability a false positive
• The vulnerability has been declared as withdrawn by a vulnerability source (NIST, OSV)
Note: this categorization for Info overrides any criteria that would place the risk into Critical, High, or Low severity.
Editing risk severities
If you decide that a different level is more appropriate for a given risk, you can manually set a new severity level. Keep in mind that doing so may impact your quality gates.
To customize the risk severity level for Software qualities impacted:
Select a risk from the search results list.
Click on the quality: Security, Reliability, or Maintainability.
Select the severity level you wish to apply from the dropdown list. You can also change the severity level from the risk’s details page.
Note that if you manually update the severity level for a risk, it will no longer be updated automatically by Sonar, even if the data used in the severity calculation changes.
How can I fix it?
Vulnerability
The How can I fix it? tab displays information about dependency versions, starting with the latest, and available fixes.
The following options are available:
Complete fix: A dependency version that fixes all associated vulnerabilities.
Partial fix: A dependency version that fixes the vulnerability but not all other vulnerabilities associated with the dependency.
Affected version: A dependency version for which the vulnerability was detected.
Malicious package
Any machine that has an installed a malicious piece of software should be considered compromised and remediated immediately. The How can I fix it? tab provides steps that should be followed when malware is detected, including informing your information security team.
Prohibited license
The dependency risk for prohibited license risk type depends on the configuration of your instance’s license profile and policy. The How can I fix it? tab provides information about different license categories and links to relevant resources. In general, resolving a license risk will require choosing a different software package to use instead. For more information, see Managing license profiles and policies.
Setting a license profile and policy
Instance admins can configure a license profile and policy to define which licenses are allowed or prohibited for the dependencies used in your projects or the whole instance. For more information, see Managing license profiles and policies.
Dependency risks in quality gates
The Project overview page displays dependency risks and indicates whether they pass or fail the associated quality gate.
As a quality gate administrator, you can configure quality gate conditions for Prohibited license, Malicious package, and Vulnerability types for new and overall code, or set limits on the number or severity of dependency risks that will cause the quality gate to fail. See Managing custom quality gates.
If your organization has recently purchased the Advanced Security package, you will have to create a custom quality gate to make sure no new dependency risks are introduced in your projects.
See Understanding measures and metrics for more information about Advanced Security metrics used in quality gates.
Downloading a dependency risk report
You can download a report of the dependency risks for your project, applications, and portfolios from the project overview page, or by calling a SonarQube Server API endpoint.
The report lists dependency risks based on the latest scan for the default branch of your project, application or portfolio. It can help managers identify:
What violations exist in their team’s projects
What patterns of risk are associated with higher-level dependencies, and how to use the information to guide developers effectively
What specific upgrades developers can perform to remove multiple violations.
The report is downloaded JSON and CSV format and contains information on:
Project, Application, Portfolio
Dependency chain(s)
Risk title (a short description of the risk)
Risk type
Risk severity
Risk status, including comments when status was changed
CVSS score associated to the risk
CVE and CWE ids, if relevant
Date when Sonar assigned the Risk to the project
Related pages
Last updated
Was this helpful?

