Disaster recovery architecture example with Azure resources
On this page
This page describes a disaster recovery example for SonarQube Server’s Data Center Edition (DCE) deployed on Kubernetes. In this example, Azure Kubernetes Service (AKS) is used, but the overall concept can be adapted to Google Cloud Platform (GCP) or Amazon Web Services (AWS) with a few modifications.
For this example, you need the Azure subscription.
Architecture overview
In our setup example, the disaster architecture consists of:
- Azure Front Door.
- Two AKS clusters (with two ingresses): your SonarQube primary and replica clusters.
- Azure Database for PostgreSQL flexible server with geo-replication and a writer endpoint.
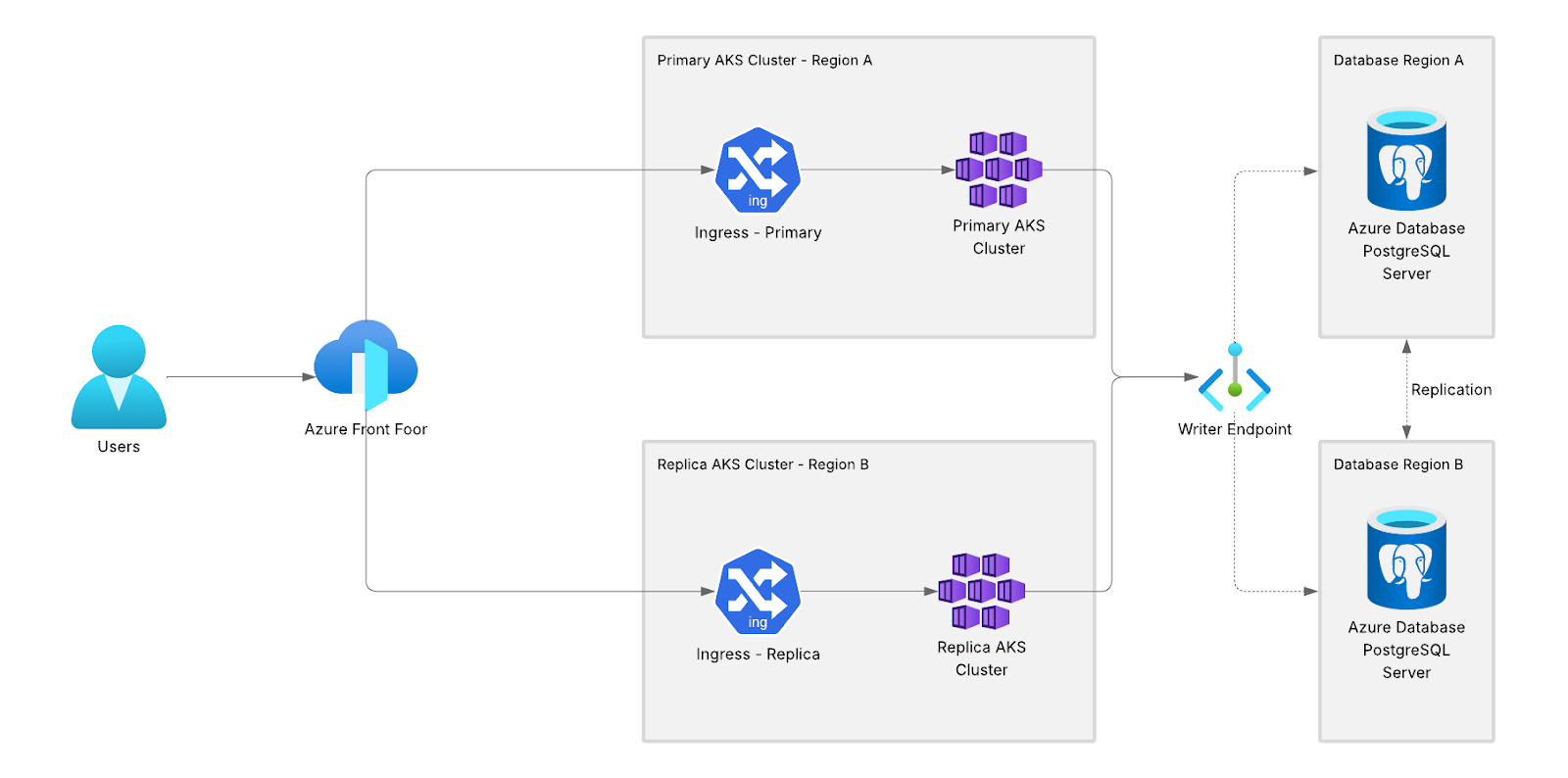
The architecture presented here represents an Active-Cold Standby configuration as SonarQube Server currently does not support access to a database in read-only format for Active/Standby or Active/Active configurations.
Disaster recovery mechanism
Azure Front Door provides a mechanism for global traffic routing and failover, which can be used in conjunction with DNS to ensure high availability:
- An endpoint is used for an origin group consisting of the two ingresses from your SonarQube primary and replica clusters.
- Priority routing is used to ensure high availability by directing traffic to your primary cluster (highest priority). If the primary cluster is unavailable, traffic automatically fails over to the replica cluster.
- An alert can be set up for your origin group that triggers whenever your primary cluster health goes under a specific threshold. The alert can optionally send an email to the SonarQube Server Administrator or start an automation runbook to perform additional actions. For example, the runbook powers on the replica cluster site in case of an outage of the primary cluster site.
The database failover process is entirely automated by the Azure Database for PostgreSQL flexible server.
Related pages
Was this page helpful?