Viewing a project security report
This feature is only available in the Enterprise plan.
Before you can view the Enterprise-level reports, your organization must be added to an enterprise. For more information, see the Managing your enterprise page.
Security reports help you understand where you may have issues related to the following security standards:
- OWASP Top 10 (versions 2021 and 2017)
OWASP Top 10 security standards covered by Sonar for version 2021
| Category | Python | JS/TS | Java | C# | C/C++ | PHP |
| A01:Broken Access Control |  |  |  |  |  |  |
| A02: Cryptographic Failures |  |  |  |  |  |  |
| A03: Injection |  |  |  |  |  | |
| A04: Insecure Design |  |  |  |  |  |  |
| A05: Security Misconfiguration |  |  |  |  |  |  |
| A06: Vulnerable and Outdated Components |  |  | ||||
| A07: Identification and Authentication Failures |  |  |  |  |  |  |
| A08: Software and Data Integrity Failures |  |  |  |  |  | |
| A09: Security Logging and Monitoring Failures |  |  |  |  |  | |
| A10: Server-Side Request Forgery |  |  |  |  |  |
- CWE Top 25 (versions 2023, 2022, and 2021)
CWE Top 25 security standards covered by Sonar for version 2023
| Category | Python | JS/TS | Java | C# | C/C++ | PHP |
| CWE-787: Out-of-bounds Write |  | |||||
| CWE-79: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') |  |  |  |  |  | |
| CWE-89: Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') |  |  |  |  |  | |
| CWE-416: Use After Free |  | |||||
| CWE-78: Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') |  |  |  |  |  | |
| CWE-20: Improper Input Validation |  |  |  |  |  | |
| CWE-125: Out-of-bounds Read |  | |||||
| CWE-22: Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') |  |  |  |  |  | |
| CWE-352: Cross-Site Request Forgery (CSRF) |  |  |  |  |  | |
| CWE-434: Unrestricted Upload of File with Dangerous Type |  | |||||
| CWE-862: Missing Authorization | ||||||
| CWE-476: NULL Pointer Dereference |  |  |  |  |  | |
| CWE-287: Improper Authentication |  | |||||
| CWE-190: Integer Overflow or Wraparound |  |  |  | |||
| CWE-502: Deserialization of Untrusted Data |  |  |  |  | ||
| CWE-77: Improper Neutralization of Special Elements used in a Command ('Command Injection') |  |  |  |  |  | |
| CWE-119: Improper Restriction of Operations within the Bounds of a Memory Buffer |  | |||||
| CWE-798: Use of Hard-coded Credentials |  |  |  |  |  |  |
| CWE-918: Server-Side Request Forgery (SSRF) |  |  |  |  |  | |
| CWE-306: Missing Authentication for Critical Function | ||||||
| CWE-362: Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition') | ||||||
| CWE-269: Improper Privilege Management |  |  | ||||
| CWE-94: Improper Control of Generation of Code ('Code Injection') |  |  |  |  |  | |
| CWE-863: Incorrect Authorization | ||||||
| CWE-276: Incorrect Default Permissions |
You can view the security report of any branch: main, long-lived, or short-lived of your project. For a given standard, it displays the number of raised security issues and hotspots by security category. Only the security rules activated in the project’s quality profiles are taken into account. See Checking the security rules included in a project’s quality profile section below.
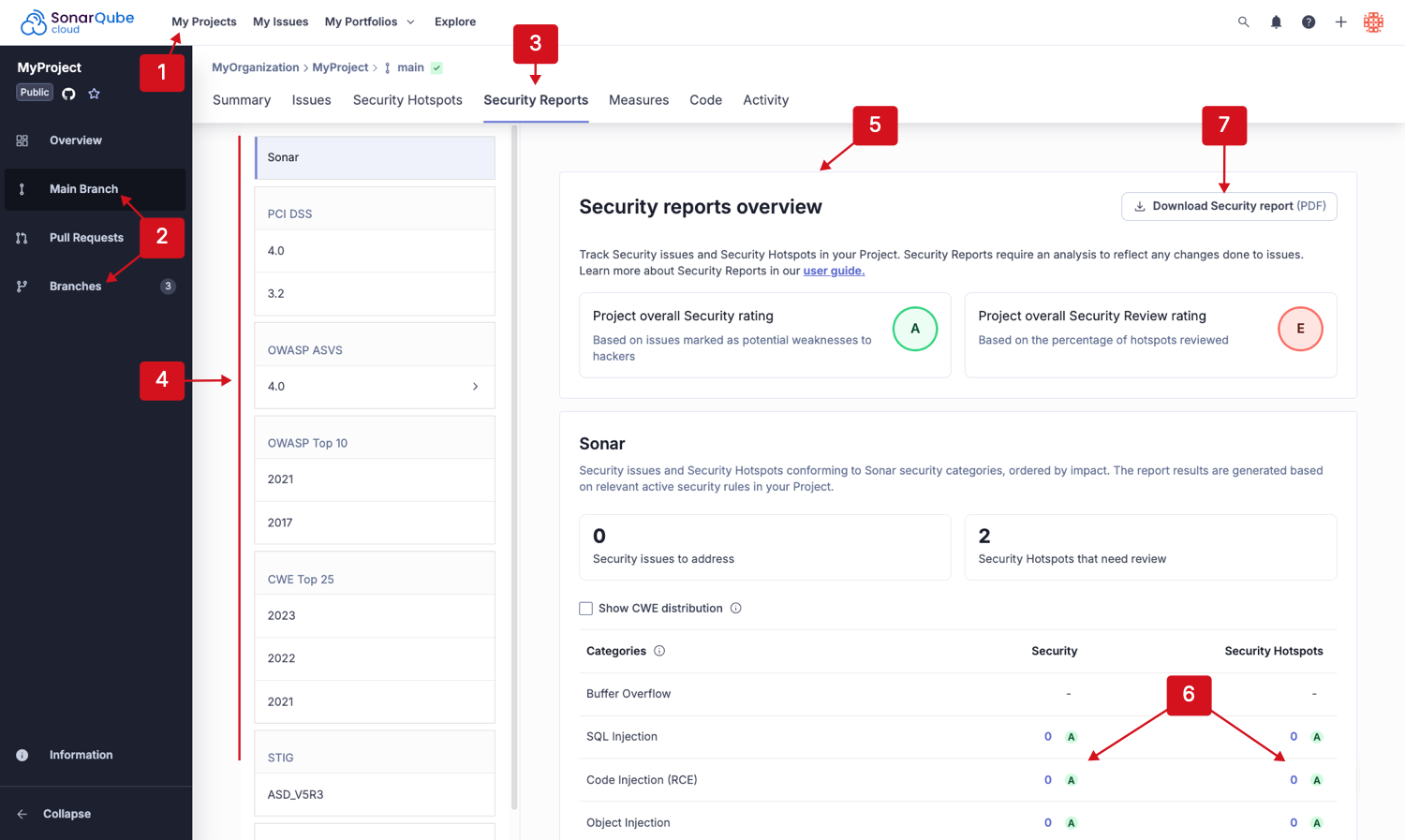
Viewing the security reports of a project branch
- Retrieve the project by going to My Projects in the top navigation bar and selecting your project.
- From the left-side panel of the project page, select a branch for which you want to view the security report. You can select:
- Main Branch
- Branches > select your branch
- Click on the Security Reports tab.
- Select the security standards you want to review. The grid displays the number of raised issues and hotspots by security category.
- View Project overall Security rating and Project overall Security Review rating in the Security reports overview section.
- Click on the number of Security issues or Security Hotspots to view more details and remedy the situation.
- Click Download Security report for a PDF version of the report.
Checking the security rules included in a project’s quality profile
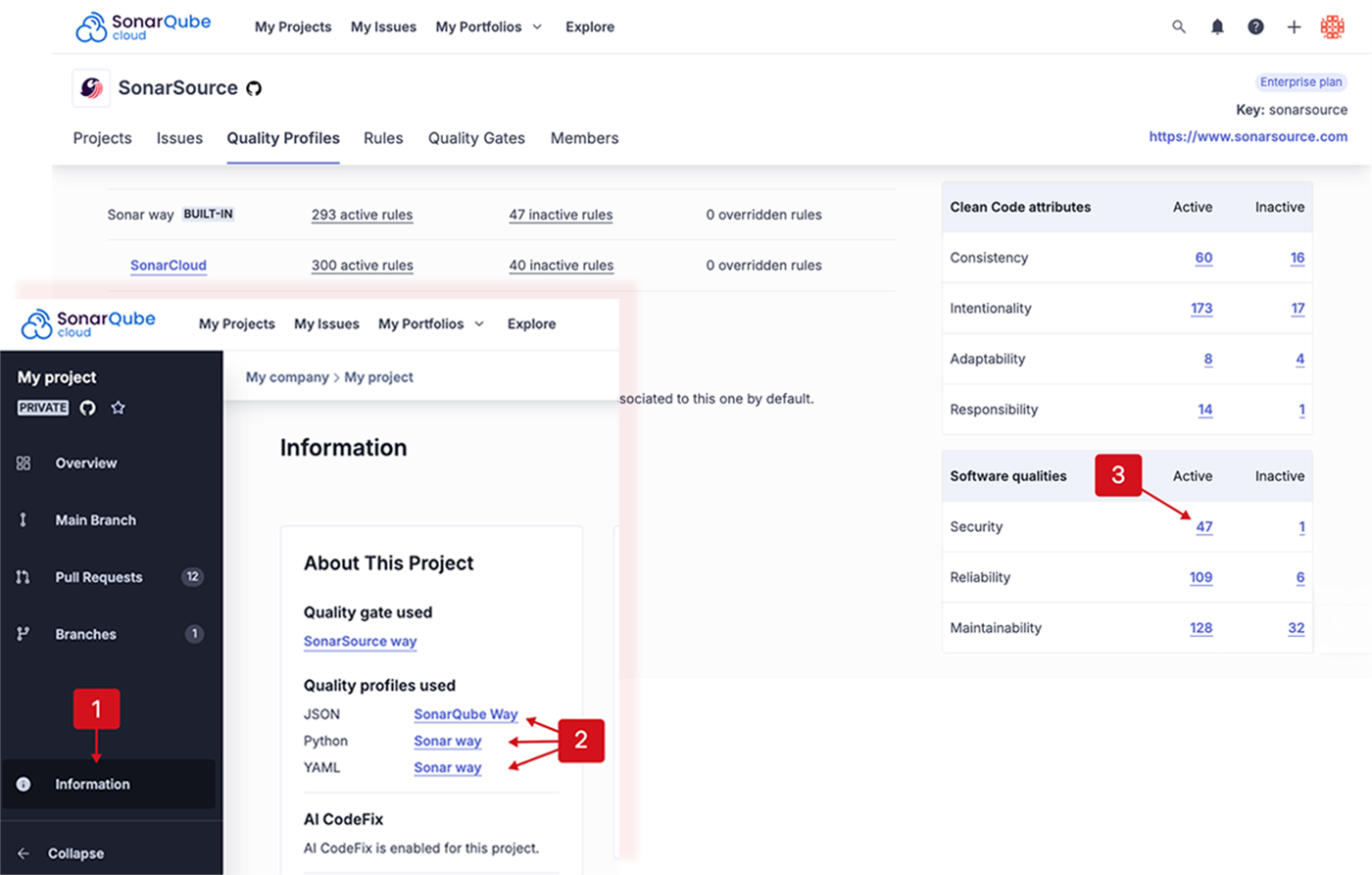
- Retrieve the project and go to the Information page.
- In About This Project, click a quality profile to open it.
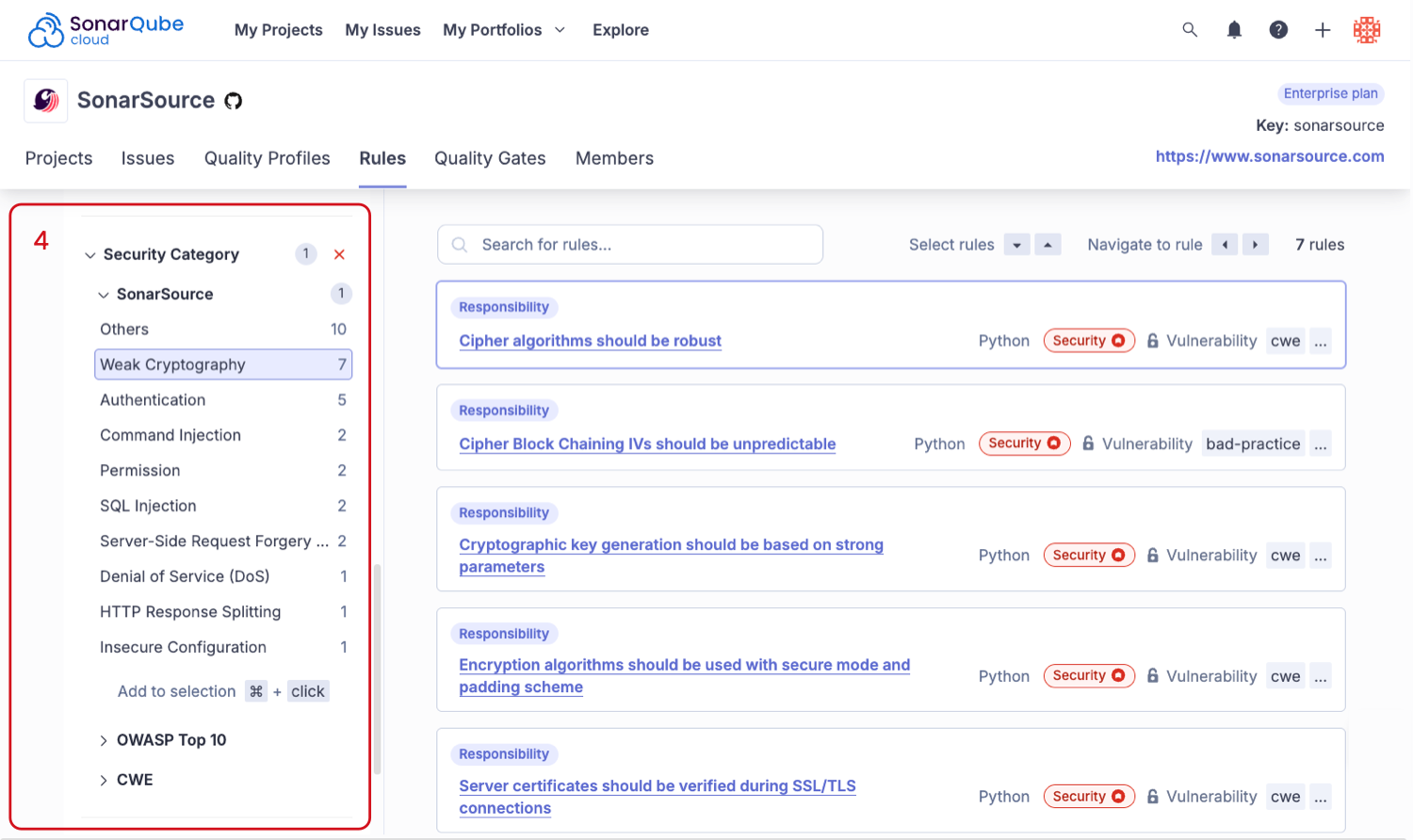
- Select the active Security rules from the Software qualities table’s Active column. The Rules page opens.
- In the left-side panel of the Rules page, scroll to the Security Category and filter the results by specific standards to view the security categories covered by code review and analysis.
Downloading a project security PDF report for a branch
As a member of a security or compliance team, you can generate and download project security reports in a PDF format for any given branch.
- Retrieve the project by going to My Projects in the top navigation bar and selecting your project.
- From the left-side panel of the project page, select a branch for which you want to view the security report. You can select:
- Main Branch
- Branches > Select your branch
- Click on the Security Reports tab.
- In the top right corner of the page click Download Security report (PDF).
Download options
The following download options are available:
- Default: Includes Sonar, OWASP top 10 2021 and CWE TOP 25 2024 security standards.
- Custom: Choose from a list of all security standards used by SonarQube.
Contents of the PDF Report
A Security Overview page that includes:
- Project and branch information
- The number of open Security issues, Security Hotspots, and Accepted Security issues on new code and overall code.
- Overall code security ratings for Security issues and Security Hotspots, including the percentage of reviewed Security Hotspots
A report for a given standard that includes:
- A list of categories for Security issues and Security Hotspots
- Number of issues to address and their relevant rating per category
- Breakdown by severity (Blocker, High, Medium, Low, Info)
- Hotspots that need review
Related pages
Was this page helpful?